https://docs.google.com/file/d/0BxCu7Tg_XCaFLWNjRjZWdlFpME0/edit?usp=sharing
IS-GTU paper Nov/Dec-2011= https://docs.google.com/file/d/0BxCu7Tg_XCaFd2cxU1FQN0ZOb28/edit?usp=sharing
IS-GTU paper May 2011= https://docs.google.com/file/d/0BxCu7Tg_XCaFaWhGYlkwOEJ6dTA/edit?usp=sharing
IS-GTU paper MAY- 2012= https://docs.google.com/file/d/0BxCu7Tg_XCaFV0h6dWk1SW12UVU/edit?usp=sharing
information
Data that is (1) accurate and timely,
(2) specific and organized for a
purpose, (3) presented within a context that gives it
meaning and relevance, and (4) can lead to an increase in understanding and decrease in uncertainty. Information is valuable because it can affect behavior, a decision, or an outcome.
When
information is entered into and stored in a computer, it is generally referred
to as data. After processing
(such as formatting and printing), output data can again be perceived as
information.
What
is Network Security?
Networks
security is concerned with protecting a network from unauthorized accesses. The
first step of this process is authenticating a user. Typically a username and a
password are used for this. This is called one-factor authentication. In
addition you can use two-factor or three-factor authentication schemes that
involves verifying fingerprints or security tokens. After authenticating a
user, a firewall is used to make sure that the user accesses only the services
that are authorized to her. In addition to authenticating users, network should
also provide security measures against computer viruses, worms or Trojans. To
protect a network from these antivirus software and intrusion prevention
systems (IPS) can be used. As mentioned earlier, different types of networks
require different levels of security. For a small network of a home or a small
business, a basic firewall, antivirus software and robust passwords would
suffice, whereas a network of an important government organization might need
to be protected using a strong firewall and proxy, encryption, strong antivirus
software and a two- or three-factor authentication system, etc.
What
is Information Security?
Information
security is concerned with protecting information from getting in to the hands
of unauthorized parties. Traditionally, main principles of information security
are considered as providing confidentiality, integrity and availability.
presently,
some other elements like possession, authenticity and utility were proposed.
Confidentiality
concerns with preventing information from going in to unauthorized parties.
Integrity makes sure that information cannot be modified secretly. Availability
is concerned with whether the information is available when they are required.
Availability also makes sure that the information system is not susceptible to
attacks like denial-of-service (DOS). Authenticity is important for verifying
the identities of two parties involved in a communication (that carry
information). In addition, information security uses cryptography, especially
when transferring information. Information would be encrypted such that it
would be unusable to anyone other than the authorized users.
What
is the difference between Network Security and Information Security?
Network security involves methods or practices
used to protect a computer network from unauthorized accesses, misuses or
modifications, whereas Information security prevents unauthorized accesses,
misuses and modifications to information systems. In practice, software and
tools used for achieving network security and information security might
overlap. For example, antivirus software, firewalls and authentication schemes
have to be employed by both the tasks. But the goals tried to be achieved by
using them are different. Further, these two tasks complement each other in the
sense if you cannot make sure that the network is secure, you can never
guarantee that the information in the network is secure.
----------------------- Unit -1-------------------------
--------------unit - 2-----------
1:- DES
2:- IDEA
3:- SimpleDES
-------------------------------------unit-9----------------
Secure
Electronic Transaction
•
Developed by Visa and MasterCard
•
Designed to protect credit card transactions
•
Confidentiality: all messages encrypted
•
Trust: all parties must have digital certificates
•
Privacy: information made available only when and where necessary
Purpose
The purpose
of the SET protocol is to establish payment transactions that
1 provide
confidentiality of information;
2 ensure the
integrity of payment instructions for goods and services order data;
3
authenticate both the cardholder and the merchant .
Participants
in the SET System
Main Entities
There are
four main entities in SET:
1. Cardholder (customer)
2. Merchant (web server)
3. Merchant’s Bank (payment gateway, acquirer): payment gateway
is a device operated by an acquirer. Sometime, separate these two entities.
4.
Issuer
(cardholder’s bank)
5.
Aacquiring bank (or acquirer)
is the bank or financial institution
that processes credit and
or debit card payments
for products or services for a merchant. The best-known (credit) card
associations are Visa, MasterCard, American Express,
How it Works
Both cardholders and merchants must
register with CA (certificate
authority) first, before they can buy
or sell on the Internet, which we will
talk about later. Once registration is
done, cardholder and merchant can
start to do transactions, which involve
9 basic steps in this protocol, which
is simplified.
1. Customer browses website and decides
on what to purchase
2. Customer sends order and payment
information, which includes 2
parts in one message:
a. Purchase Order – this part is for
merchant
b. Card Information – this pat is for
merchant’s bank only.
3. Merchant forwards card information
to their bank
4. Merchant’s bank checks with Issuer for
payment authorization
5. Issuer send authorization to
Merchant’s bank
6. Merchant’s bank send authorization
to merchant
7. Merchant completes the order and
sends confirmation to the
customer
8. Merchant captures the transaction
from their bank
9. Issuer prints credit card bill (invoice) to customer
Firewall
Design Principles
•
Effective
means of protection a local system or network of systems from network_based
security threats while affording access to the outside world via WAN’s or the
Internet.
Firewall Design Principles
•
Strong security features for all workstations and servers not
established
•
The firewall is inserted between the grounds network and the
Internet
•
All traffic from inside to outside must pass through the firewall (physically
blocking all access to the local network except via the firewall)
•
Only authorized traffic (defined by the local security police)
will be allowed to pass
•
The firewall itself is resistant to access (use of trusted system
with a secure operating system)
•
Service control:
Determines
the types of Internet services that can be accessed, inbound or outbound
•
Direction control:
Determines
the direction in which particular service requests are allowed to flow
•
User control:
Controls
access to a service according to which user is attempting to access it
•
Behavior control:
Controls how
particular services are used (e.g. filter e-mail)
Types of Firewalls
•
Three common types of Firewalls:
–
Packet-filtering routers
–
Circuit level
–
Application-level gateways
Packet Filter
•
Work at the network level of the OSI model
•
Each packet is compared to a set of criteria before it is
forwarded
•
Packet filtering firewalls is low cost and low impact on network
performance
Figure :
Packet Filter
Circuit level
•
Circuit level gateways work at the session layer of the OSI model,
or the TCP layer of TCP/IP
•
Monitor TCP handshaking between packets to determine whether a
requested session is legitimate.
Figure :
Circuit level
Application Level
•
Application level gateways, also called proxies, are similar to
circuit-level gateways except that they are application specific
•
Gateway that is configured to be a web proxy will not allow any
ftp, gopher, telnet or other traffic through
Assignment 1
1) Explain single round function of DES with suitable diagram
2) Explain international Data encryption Algorithm .
3) Explain Deffie Hellman key Exchange scheme in detail.
4) give the step of RSA algorithm with example.
5) Explain ECC.
IS Programs
c program to compare two strings
A-
C program to compare two strings using strcmp
#include<stdio.h> #include<string.h> main() { char a[100], b[100]; printf("Enter the first string\n"); gets(a); printf("Enter the second string\n"); gets(b); if( strcmp(a,b) == 0 ) printf("Entered strings are equal.\n"); else printf("Entered strings are not equal.\n"); return 0; }
B- C program to compare two strings without using strcmp
int compare(char a[], char b[]) { int c = 0; while( a[c] == b[c] ) { if( a[c] == '\0' || b[c] == '\0' ) break; c++; } if( a[c] == '\0' && b[c] == '\0' ) return 0; else return -1; }
C- C program to compare two strings using pointers
#include<stdio.h> int compare_string(char*, char*); main() { char first[100], second[100], result; printf("Enter first string\n"); gets(first); printf("Enter second string\n"); gets(second); result = compare_string(first, second); if ( result == 0 ) printf("Both strings are same.\n"); else printf("Entered strings are not equal.\n"); return 0; } int compare_string(char *first, char *second) { while(*first==*second) { if ( *first == '\0' || *second == '\0' ) break; first++; second++; } if( *first == '\0' && *second == '\0' ) return 0; else return -1; }
2)
User Authentication to access secured resources
/* This program is to illustrate how user authentication *
* is made before allowing the user to access the secured *
* resources. It asks for the user name and then the *
* password. The password that you enter will not be *
* displayed, instead that character is replaced by '*' */#include <stdio.h>
#include <conio.h>
void main()
{
char pasword[10],usrname[10], ch;
int i;
clrscr();
printf("Enter User name: ");
gets(usrname);
printf("Enter the password <any 8 characters>: ");
for(i=0;i<8;i++)
{
ch = getch();
pasword[i] = ch;
ch = '*' ;
printf("%c",ch);
}
pasword[i] = '\0';
/*If you want to know what you have entered as password, you can print it*/
printf("\nYour password is :");
for(i=0;i<8;i++)
{
printf("%c",pasword[i]);
}
}
/*-----------------------------------------------
Output
Enter User name: bharad
Enter the password <any 8 characters>: ********
Your password is :GKB12345
-----------------------------------------------*/
Practical – 1
AIM: introduction of basic encryption and decryption.
Ø Basic Vocabulary of Encryption and Decryption
plaintext: This is what you want to encrypt
ciphertext: The encrypted output
enciphering or encryption: The process by which plaintext is converted into ciphertext
encryption algorithm: The sequence of data processing steps that go into transforming plaintext into ciphertext. Various parame- ters used by an encryption algorithm are derived from a secret key. In cryptography for commercial and other civilian applications, the encryption and decryption algorithms are made public.
secret key: A secret key is used to set some or all of the various parameters used by the encryption algorithm. The impor tant thing to note is that, in classical cryptography,
the same secret key is used for encryption and decryption. It is for this reason that classical cryptography is also referred to as symmetric key cryptography. On the other hand, in the more modern cryptographic algorithms, the encryption and decryption keys are not only different, but also one of them is placed in the public domain. Such algorithms are commonly referred to as asymmetric key cryptography.
decryption algorithm: The sequence of data processing steps that go into transforming ciphertext back into plaintext. In classifical cryptography, the various parameters used by a decryption algorithm are derived from the same secret key that was used in the encryption algorithm.
cryptography: The many schemes available today for encryption and decryption
cryptographic system: Any single scheme for encryption
cipher: A cipher means the same thing as a “cryptographic system”
block cipher: A block cipher processes a block of input data at a
time and produces a ciphertext block of the same size.
stream cipher: A stream cipher encrypts data on the fly, usually one byte at at time.
cryptanalysis: Means “breaking the code”. Cryptanalysis relieson a knowledge of the encryption algorithm and some knowledge of the possible structure of the plaintext (such as the structure of a typical inter-bank financial transaction) for a partial or full reconstruction of the plaintext from ciphertext. Additionally, the goal is to also infer the key for decryption of future messages. The precise methods used for cryptanalysis depend on whether the “attacker” has just a piece of ciphertext, or pairs of plaintext and ciphertext, how much structure is possessed by the plaintext, and how much of that structure is known to the attacker.
Ø Encryption and decryption
In cryptography, encryption is the process of encoding messages (or information) in such a way that eavesdroppers or hackers cannot read it, but that authorized parties can. In an encryption scheme, the message or information (referred to as plaintext) is encrypted using an encryption algorithm, turning it into an unreadable ciphertext . This is usually done with the use of an encryption key, which specifies how the message is to be encoded. Any adversary that can see the ciphertext should not be able to determine anything about the original message. An authorized party, however, is able to decode the ciphertext using a decryption algorithm, that usually requires a secret decryption key, that adversaries do not have access to. For technical reasons, an encryption scheme usually needs a key-generation algorithm to randomly produce keys.
Data that can be read and understood without any special measures is called plaintext or cleartext. The method of disguising plaintext in such a way as to hide its substance is called encryption. Encrypting plaintext results in unreadable gibberish called ciphertext. You use encryption to ensure that information is hidden from anyone for whom it is not intended, even those who can see the encrypted data. The process of reverting ciphertext to its original plaintext is called decryption.
plaintext ciphertext plaintext
encryption decryption
Figure 1-1. Encryption and decryption
Ø Conventional cryptography
In conventional cryptography, also called secret-key or symmetric-key encryption, one key is used both for ncryption and decryption. The Data Encryption Standard (DES) is an example of a conventional cryptosystem that is widely employed by the Federal Government. Figure 1-2 is an illustration of the conventional encryption process.
plaintext ciphertext plaintext
encryption decryption
Figure 1-2. Conventional encryption
==================================
Practical – 2
Aim: Write a C program for Caesar Cipher.
Source code
#include<stdio.h>
#include<conio.h>
#include<string.h>
void main()
{
char mt[15];
int a[100],i,j,k,b[100];
clrscr();
printf("enter any text\n");
scanf("%s",&mt);
printf("enter the key\n");
scanf("%d",&k);
printf("the cipher text is\n");
j=0;
for(i=0;mt[i]!='\0';i++)
{
j++;
a[i]=((int)mt[i])+k;
if(a[i]>122)
{
a[i]=a[i]-26;
}
printf("%c",a[i]);
}
printf("\nthe decipher text is\n");
for(i=0;i<=j-1;i++)
{
b[i]=(a[i]-k);
if(b[i]<97)
{
b[i]=b[i]+26;
}
b[i]=((char)b[i]);
printf("%c",b[i]);
}
getch();
}
Output
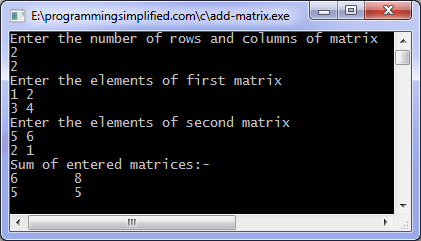
 c program to add two matrix
c program to add two matrix
Practical – 4
Aim: Write a C program for Polyalphabatic Cipher.
Source Code:
#include<stdio.h>
#include<conio.h>
#include<string.h>
char pt[40]={'\0'},key[40]={'\0'},ct[40]={'\0'},pta[40]={'\0'},k[40]={'\0'};
int i,j;
void main()
{
clrscr();
printf("\nEnter the keyword:\n");
gets(k);
printf("\nEnter the Plain text:\n");
gets(pt);
printf("The convergen matrix\n");
printf("\n ");
for(j=97;j<=122;j++)
{
printf(" %c",j);
}
printf("\n--------------------------------------------------------\n");
for(i=97;i<=122;i++)
{
printf("%c |",i);
for(j=97;j<=122;j++)
{
if(((i+j))>219)
printf(" %c",toupper((i+j)-123));
else
printf(" %c",toupper((i+j)-97));
}
printf("\n");
}
j=0;
for(i=0;i<strlen(pt);i++)
{
key[i]=k[j];
if(j==(strlen(k)-1))
j=0;
else
j++;
}
for(i=0;i<(strlen(pt)-1);i++);
k[i]='\0';
printf("\nThe encrypted text is:\n");
for(i=0;i<strlen(pt);i++)
{
if(97<=(int)pt[i] && (int)pt[i]<=122)
{
if(((int)pt[i]+(int)key[i])>219)
ct[i]=(int)pt[i]+(int)key[i]-123;
else
ct[i]=(int)pt[i]+(int)key[i]-97;
printf("%c",toupper(ct[i]));
}
else
{
ct[i]=pt[i];
printf("%c",pt[i]);
}
}
printf("\n\nDecrypted text is:\n");
for(i=0;i<strlen(ct);i++)
{
if(97<=(int)ct[i] && (int)ct[i]<=122)
{
if(((int)ct[i]-(int)key[i])<0)
pta[i]=((int)ct[i]-(int)key[i])+123;
else
pta[i]=(int)ct[i]-(int)key[i]+97;
printf("%c",pta[i]);
}
else
{
pta[i]=ct[i];
printf("%c",pta[i]);
}
}
getch();
}
---------------------------------------------------------------------------------------
AIM: Write a C program for Rail fence Algorithm (Transposition).
AIM: Write a C program for Euclid Theorem.
============================================================
practical ---------7 client server Application for Encryption and Decryption
Practical – 5
AIM: Write a C program for Rail fence Algorithm (Transposition).
Source code
#include<stdio.h>
#include<conio.h>
void main()
{
char pt[100];
char et[100]={"\0"};
char dt[100]={"\0"};
char newpt[100]={"\0"};
int len,i,j,newlen,k,m=0;
int len1,i1,j1,k1,m1=0;
clrscr();
printf("Enter Plain Text:");
gets(pt);
//blank space remove
len=strlen(pt);
for(i=0;i<len;i++)
{
if(pt[i] != 32)
{
newlen=strlen(newpt);
newpt[newlen]=pt[i];
}
}
//encryption
len=strlen(newpt);
if(len%2==0)
k = len/2;
else
k = len/2 + 1;
for(j=0;j<len;j++)
{
if(j%2 == 0)
{
et[m]=newpt[j];
m++;
}
else
{
et[k] = newpt[j];
k++;
}
}
printf("Encrypted text is:%s",et);
//decryption
len1=strlen(et);
if(len1%2==0)
k1 = len1/2;
else
k1 = len1/2 + 1;
for(j1=0;j1<len1;j1++)
{
if(j1%2 == 0)
{
dt[j1]=et[m1];
m1++;
}
else
{
dt[j1] = et[k1];
k1++;
}
}
printf("\nDecrypted text is:%s",dt);
getch();
}
===========================================================
Practical – 6
AIM: Write a C program for Euclid Theorem.
Source code
#include<stdio.h>
#include<conio.h>
int euclid(int a,int b)
{
if(b==0)
return a;
else
return euclid(b,a%b);
}
void main()
{
int n1,n2;
clrscr();
printf("Enter two numbers to find its GCD:");
scanf("%d %d",&n1,&n2);
printf("The GCD of %d and %d is %d",n1,n2,euclid(n1,n2));
getch();
}
============================================================
practical ---------7 client server Application for Encryption and Decryption
=============================================================
practical -------- 8 RSA
#include<stdio.h>
#include<conio.h>
void main()
{
int i,p,q,z,t,e,d;
long ct=1,n,o=1,pt;
clrscr();
printf("enter two large prime no:");
scanf("%d %d",&p,&q);
printf("enter pt");
scanf("%d",&pt);
n=p*q;
printf("\n n is %d",n);
t=(p-1)*(q-1);
printf("\n t is %d\n",t);
for(i=2;i<t;i++)
{
z=t%i;
if(z!=0)
{
printf(" %d ",i);
}
} */
/* for(i=2;i<=t;i++)
{
if(t%i == 0)
{
printf(" %d ",i);
t=t/i;
i--;
}
}
*/
printf("\nenter any one above number");
scanf("%d",&e);
printf("\ne is %d",e);
for(i=1;;i++)
{
if(((i*e)%t)==1)
{
d=i;
break;
}
}
printf("\nd is %d",d);
for(i=0;i<e;i++)
{
ct=(ct*pt)%n;
}
printf("\nct is %d",ct);
pt=1;
for(i=0;i<d;i++)
{
pt=(pt*ct)%n;
}
printf("\npt is %d",pt);
getch();
}
===============================================================
Practical – 9
AIM: Write a C program to perform Diffie-Hellman Key Exchange Algorithm.
Source code
#include <stdio.h>
#include <conio.h>
#include <math.h>
void main()
{
int q,alpha,xa,xb,ya,yb,ka,kb,x,y,z,count,ai[20][20];
clrscr();
printf("Enter a Prime Number \"q\":");
scanf("%d",&q);
printf("Enter a No \"xa\" which is less than value of q:");
scanf("%d",&xa);
printf("Enter a No \"xb\" which is less than value of q:");
scanf("%d",&xb);
for(x=0;x<q-1;x++) //Primitive Root Calculation
for(y=0;y<q-1;y++)
ai[x][y] = ((int)pow(x+1,y+1))%q;
for(x=0;x<q-1;x++)
{
count = 0;
for(y=0;y<q-2;y++)
{
for(z=y+1;z<q-1;z++)
if(ai[x][y] == ai[x][z])
{
count = 1;
break;
}
if(count == 1)
break;
}
if (count == 0 )
{
alpha = x+1;
break;
}
}
printf("alpha = %d\n",alpha);
ya = ((int)pow(alpha,xa))%q;
yb = ((int)pow(alpha,xb))%q;
ka = ((int)pow(yb,xa))%q;
kb = ((int)pow(yb,xb))%q;
printf("ya = %d\nyb = %d\nka = %d\nkb = %d\n",ya,yb,ka,kb);
if(ka == kb)
printf("The keys exchanged are same");
else
printf("The keys exchanged are not same");
getch();
}
--------------------------------------- 0r----------------------------------------------
C/C++ Program for Implementation of Diffie Hellman Key Exchange Algorithm
#include<conio.h>
#include<iostream.h>
#include<math.h>
int alice(int,int,int);
int bob(int,int,int);
void main()
{
long int g,x,y,a,b,k1,k2,n;
clrscr();
cout<<"\n\t Enter value of n & g";
cin>>n>>g;
cout<<"\n\t Enter value of x & y";
cin>>x>>y;
a=alice(n,g,x);
cout<<"\n\t alice end value:"<<a;
b=bob(n,g,y);
cout<<"\n\t bob end value:"<<b;
k1=alice(n,b,x);
cout<<"\n\t valueof k1 :"<<k1;
k2=alice(n,a,y);
cout<<"\n\t valueof k2 :"<<k2;
getch();
}
int alice(int n,int g,int x)
{
long int a,a1;
a1=pow(g,x);
a=a1%n;
return(a);
}
int bob(int n,int g,int y)
{
long int b,b1,k2,t2;
b1=pow(g,y);
b=b1%n;
return(b);
}
10 kerberos
Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. It has the following characteristics:
• It is secure: it never sends a password unless it is encrypted.
• Only a single login is required per session. Credentials defined at login are then passed between resources without the need for additional logins.
• The concept depends on a trusted third party – a Key Distribution Center (KDC). The KDC is aware of all systems in the network and is trusted by all of them.
• It performs mutual authentication, where a client proves its identity to a server and a server proves its identity to the client.
Kerberos introduces the concept of a Ticket-Granting Server (TGS). A client that wishes to use a service has to receive a ticket – a time-limited cryptographic message – giving it access to the server. Kerberos also requires an Authentication Server (AS) to verify clients. The two servers combined make up a KDC. Active Directory performs the functions of the KDC. The following figure shows the sequence of events required for a client to gain access to a service using Kerberos authentication. Each step is shown with the Kerberos message associated with it, as defined in RFC 4120 “The Kerberos Network Authorization Service (V5)”.
• Step 1: The user logs on to the workstation and requests service on the host. The workstation sends a message to the Authorization Server requesting a ticket granting ticket (TGT).
• Step 2: The Authorization Server verifies the user’s access rights in the user database and creates a TGT and session key. The Authorization Sever encrypts the results using a key derived from the user’s password and sends a message back to the user workstation.
The workstation prompts the user for a password and uses the password to decrypt the incoming message. When decryption succeeds, the user will be able to use the TGT to request a service ticket.
• Step 3: When the user wants access to a service, the workstation client application sends a request to the Ticket Granting Service containing the client name, realm name and a timestamp. The user proves his identity by sending an authenticator encrypted with the session key received in Step 2.
• Step 4: The TGS decrypts the ticket and authenticator, verifies the request, and creates a ticket for the requested server. The ticket contains the client name and optionally the client IP address. It also contains the realm name and ticket lifespan. The TGS returns the ticket to the user workstation. The returned message contains two copies of a server session key – one encrypted with the client password, and one encrypted by the service password.
• Step 5: The client application now sends a service request to the server containing the ticket received in Step 4 and an authenticator. The service authenticates the request by decrypting the session key. The server verifies that the ticket and authenticator match, and then grants access to the service. This step as described does not include the authorization performed by the Intel AMT device, as described later.
• Step 6: If mutual authentication is required, then the server will reply with a server authentication message.
The Kerberos server knows "secrets" (encrypted passwords) for all clients and servers under its control, or it is in contact with other secure servers that have this information. These "secrets" are used to encrypt all of the messages shown in the figure above.
To prevent "replay attacks," Kerberos uses timestamps as part of its protocol definition. For timestamps to work properly, the clocks of the client and the server need to be in synch as much as possible. In other words, both computers need to be set to the same time and date. Since the clocks of two computers are often out of synch, administrators can establish a policy to establish the maximum acceptable difference to Kerberos between a client's clock and server's clock. If the difference between a client's clock and the server's clock is less than the maximum time difference specified in this policy, any timestamp used in a session between the two computers will be considered authentic. The maximum difference is usually set to five minutes.
Note that if a client application wishes to use a service that is "Kerberized" (the service is configured to perform Kerberos authentication), the client must also be Kerberized so that it expects to support the necessary message responses.







thanks for the info.....
ReplyDelete